Can You Trust Your Providers?
Cyber incidents, caused by bad practice.
You may wonder how so many cyber breaches occur, and the answer is usually down to a misconfiguration, or a vulnerability discovered in a piece of software. One of the most common sources of these misconfigurations is third party software vendors, especially niche vendors. Due to legacy requirements, outdated capabilities or just plain bad practice, these vendors often ask you to actively compromise your own environment to enable their software to function.
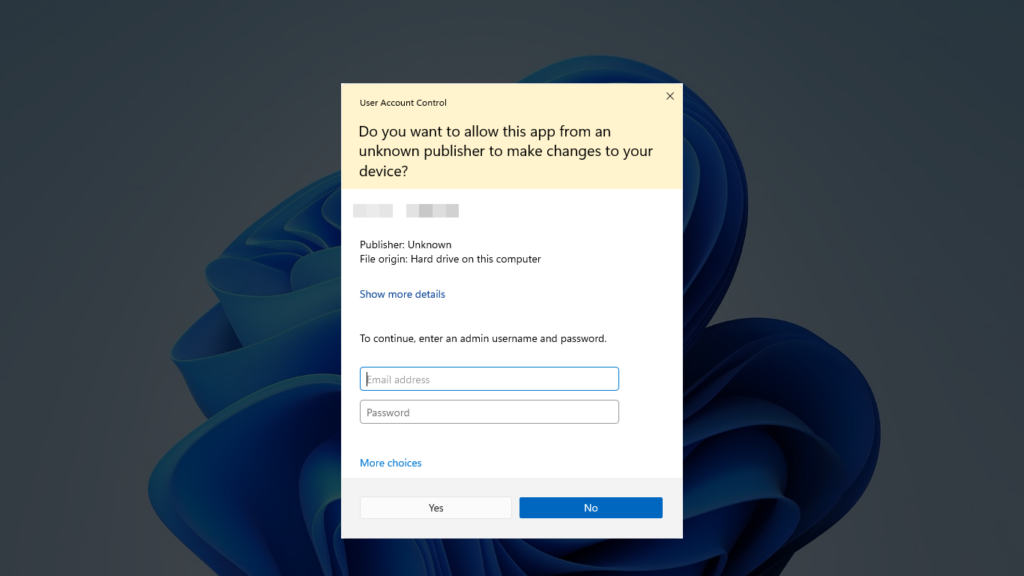
Change a few settings? Sure!
If you’ve spent any time around legacy or niche software, typically specific to a certain industry, you may have stumbled upon requests from those vendors when installing or updating their software, such as disabling windows firewall or disabling the UAC prompt (that annoying popup in Windows when you want to make administrative changes), but are you aware of the potential impact of these changes? The answer is almost always no. The reality is that these changes are often the way networks are exploited and compromised.
Updating niche software can be costly, is it worth it?
If you’re in the situation where upgrading the software can be costly, you may be wondering what benefits those costs bring? Primarily, these upgrades ensure access to the latest features and functionalities, enhancing overall productivity and efficiency within the organisation. By staying current with software updates, businesses often receive security patches and fixes, thereby fortifying their systems against potential vulnerabilities and cyber threats, safeguarding sensitive data and maintaining customer trust. Upgrades also tend to offer improved compatibility with other applications, fostering seamless integration and smoother workflows. Additionally, updated software frequently aligns with evolving industry standards and regulations, ensuring compliance and mitigating risks. Ultimately, investing in regular third-party software upgrades not only bolsters performance but also future proofs the business.
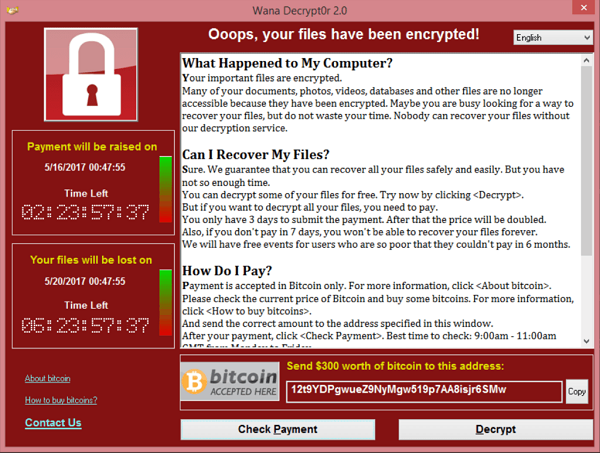
The cost of doing nothing.
The ‘WannaCry’ ransomware attack on NHS in the UK is a good example of a neglected and outdated environment, most likely left in this state due to IT and medical equipment costs to upgrade. In May 2017, the attack exploited a weakness in outdated Windows operating systems, affecting NHS computer systems nationwide. This malicious software encrypted data, rendering crucial medical records and systems inaccessible, disrupting hospital operations, delaying patient care, and leading to cancelled appointments and diverted ambulances. The attack’s widespread impact highlighted the vulnerabilities within the healthcare sector and underscored the urgent need for robust cybersecurity measures and regular system updates to protect against such threats, especially in institutions handling sensitive patient information and essential services. The aftermath of the attack prompted increased awareness about the importance of investing in cybersecurity and emphasised the critical role of timely software updates and security patches in preventing similar large-scale disruptions in the future.
How to move forward.
The best way to handle software security issues is to pick trustworthy companies that make safe and up-to-date software. But sometimes, you might be stuck with software that can’t be updated. If that happens, it’s important to know the risks. One way to deal with this is to keep those devices or software separate from the rest of your network. It’s like putting them in a different room where they can’t easily interact with the rest of your infrastructure. This helps lower the chance of problems from spreading if there’s a security issue with that particular software. It’s not a perfect fix, but it can help protect your important information.
The BITS team are experienced in working with a wide range of common and niche software, especially in healthcare, dental, optometric, veterinary, construction, legal and finance industries. If you would like more information or have questions about your IT environment, email sales@bitsgroup.com.au



